AI-Based Strategic Cyber Defense Planning & Optimization (CDPO) Platform
SAGE Gives CISOs Data-Driven Defense Strategies Tailored to Best Practices
The SAGE platform empowers CISOs by providing strategic cyber defense planning capabilities and dynamic risk analysis.
SAGE’s capabilities include context-based decision support and automated budgeting simulations to facilitate clear communication between security team leaders and business stakeholders.
The result is a noticeable increase in your cybersecurity readiness.
Why SAGE for Cyber Defense Planning?
While working closely with CISOs, our team identified a core need: to design, build and maintain an effective and efficient defense plan. Most CISOs are:
- Building and operating their defense plan on manual/ static documents
- Unable to analyze and respond to the huge amounts of data from various reports and intelligence sources (Internal and external
- Challenged to communicate cyber risks and business impact to boards, Sr. management and other stakeholders
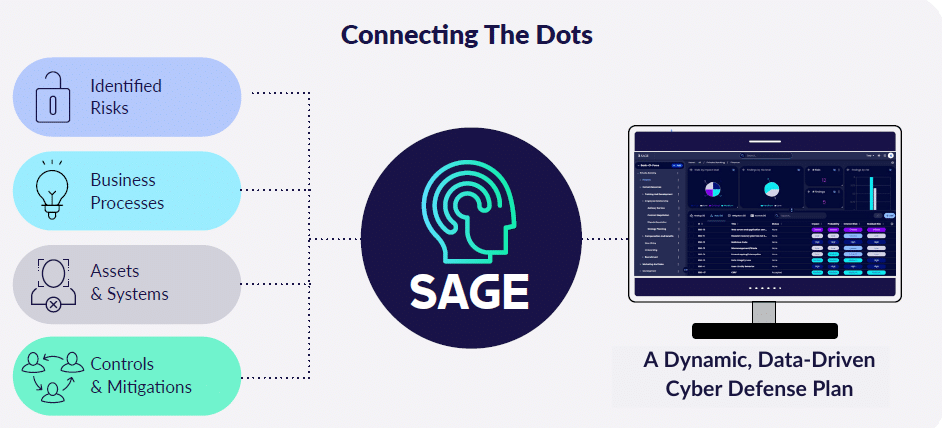
SAGE is purpose built for CISOs. It considers the needs of the organization: business impact analysis, risk tolerance, cyber posture, attack surface, etc., then considers attack vectors and analyzes everything with HolistiCyber’s unique methods in seeing the attack surface the way an attacker would.
Cyber Defense Platform Applications
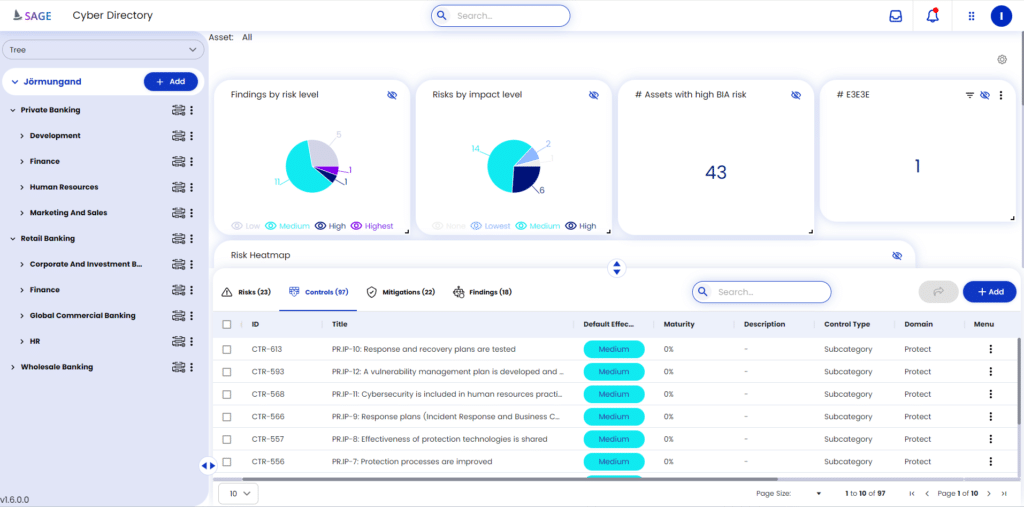
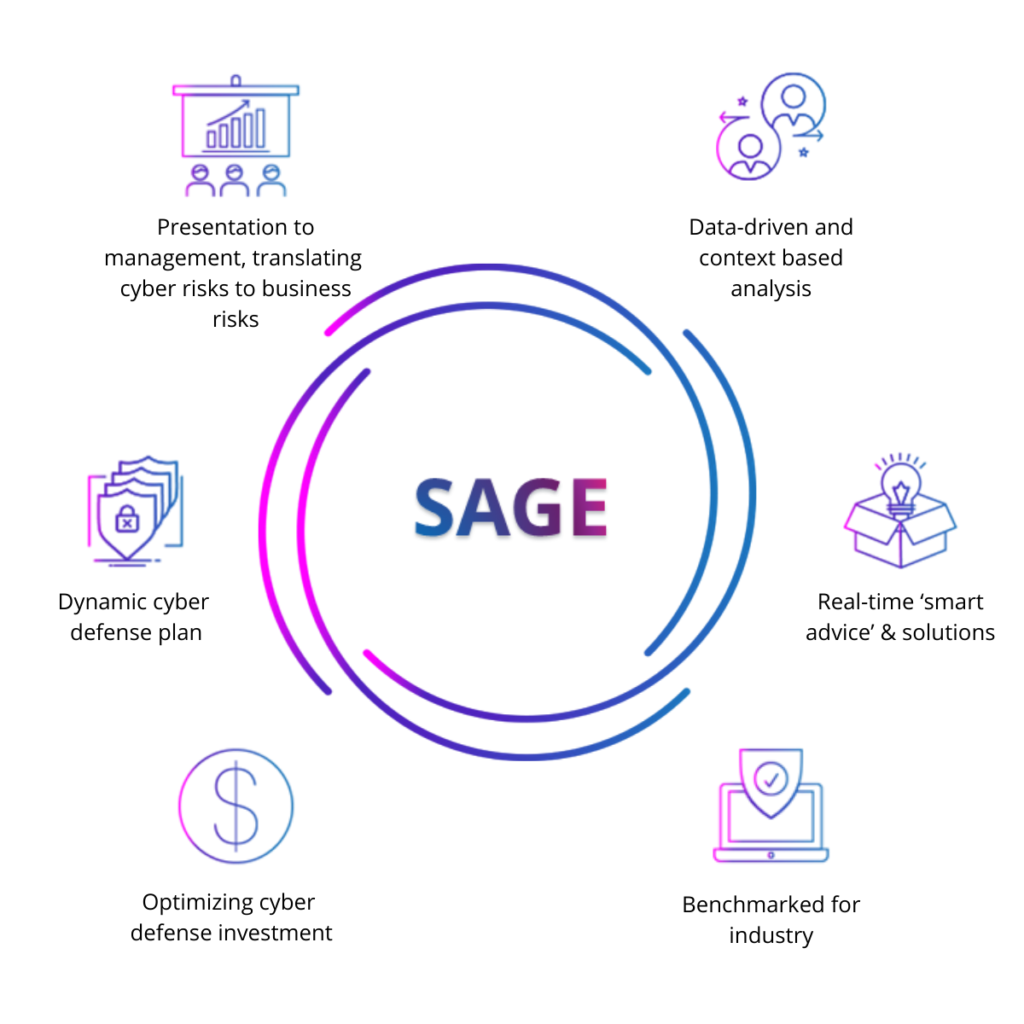
SAGE includes a context map of everything that matters – risks, vulnerabilities, assets, cyber-threats, and how they impact the business. The platform provides simple presentation options for management, translating cyber risks into business risks and includes “what-if” analysis to optimize budget usage for cyber security.
Most CISOs Are:
Reacting to cyber threats and potential breaches without a clear plan.
Hindered in their decision making by data that lacks sufficient context.
Under pressure to meet new compliance regulations and escalating demands for data privacy.
Struggling to secure buy-in from C-Suite and BODs due to inability to translate cybersecurity needs into business requirements.
Searching for a well-designed, unified tool for adaptive cybersecurity planning.



