Who better to be testing your environment than someone who used to do this on the cyber warfare front lines? Our consultants have decades of experience in actual cyber defense. Since the nation-state and nation-state grade threat is growing every day, going into an engagement with this level of expertise puts you ahead of the rest.
Penetration tests are key to understanding an organization’s vulnerabilities to nation-state level attacks, as well as specific potential attack paths and critical attack vectors.
By conducting thorough and comprehensive penetration tests, our team of experts will identify and exploit system vulnerabilities using sophisticated and advanced attack vectors. These tests go beyond surface-level assessments and delve deep into an organization’s information technology assets. By simulating realistic attack scenarios, our experts can provide a clear breakdown of your vulnerabilities and expose potential attack paths that could be exploited by nation-state level threats.
Understanding these critical attack vectors is crucial for organizations to fortify their cyber defenses against even the most crippling attacks. Our consultants, with their decades of experience in actual cyber attacking and defending, possess the knowledge and expertise needed to stay one step ahead of evolving cyber threats. By partnering with us, you gain an invaluable advantage over other organizations within your domain, as our extensive experience on the cyber warfare front lines ensures that we can accurately assess your environment and assist in creating a resilient cyber defense strategy.
Attack simulations on the organization’s IT systems – data, infrastructure, applications and people
Pragmatic and actionable results to enable your cyber defense plan
It is common to conflate the two of these since they are often used interchangeably, but there are big differences between them.
Many organizations utilize vulnerability scanning in lieu of pentest services, but it’s not a replacement. They are intended to support each other. The main difference is that vulnerability scanning is a software program, and a pentest is done by humans. Using them together is an effective way to understand where your technical vulnerabilities lie, and also how an adversary would exploit those vulnerabilities.
It’s no secret pentesting has become a compliance exercise. The board and executive management understand it’s a need to avoid those pesky fines. Especially if you are in a highly regulated industry such as finance or healthcare, pentests can be seen as more of a nuisance than a help. It has been increasingly difficult to tie them to a business context other than ticking the box for the regulatory bodies.
Considering a majority of security leaders don’t believe they’re hitting the mark, we need to reexamine how we look at pentesting services.
70% of security leaders do not believe their current pentesting service methods address priority security vulnerabilities

We believe that penetration testing services need to be much more closely tied to business objectives than simply checking a box. Our whitepaper, “Rebooting the Pentest” breaks down all four of these levels on the left.
Traditionally, security teams fall into the technical-led pentesting category – which will suffice for compliance. However, we all know the adage “an attacker doesn’t care about scope.” When we fall into a strict scope of work in an attack and penetrate scenario, there could be glaring vulnerabilities that are missed.
The more down the levels we go, the more relevant to the business it becomes. On top of that, you will have more relevant, actionable, and pragmatic solutions for remediation once the service is completed.
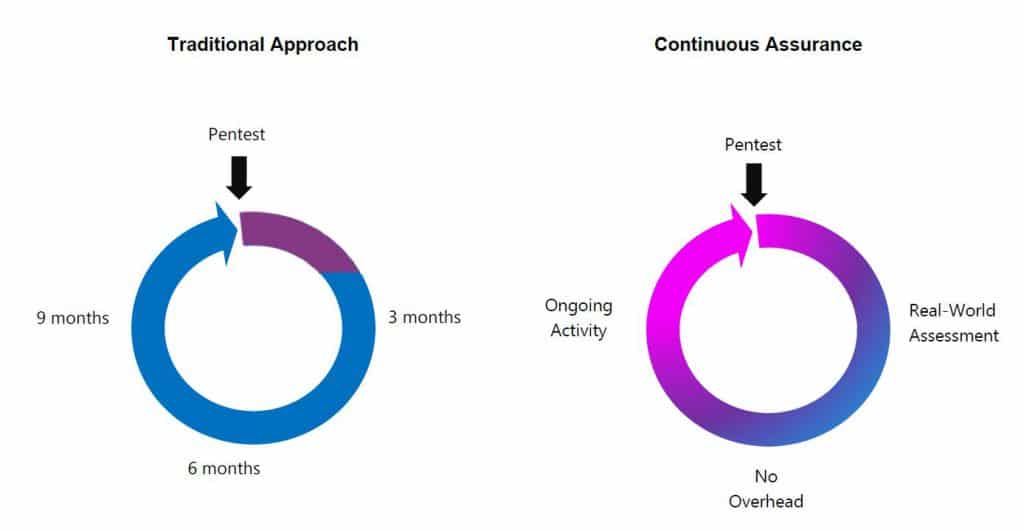
One of the most frustrating things about pentesting services is the upfront scope of work process. You have a new application that needs to be rolled out. Executive leadership is harping on you to get it done. The application has been developed but hasn’t been tested yet. You go to your vendors and discuss the issue. They then have to take it and build your scope of work. Revisions have to be made. Prices have to be negotiated. This can take weeks depending on the backlog of projects the vendor has. Rinse and repeat any time there is a software update.
Continuous assurance remediates that.
© 2025 Holistic Cyber (HolistiCyber). All Rights Reserved. Privacy Policy