Why do so many enterprises wait for disaster to hit, for a catastrophic ransomware attack to take place before they finally take action to defend their critical assets?
The cost of a ransomware attack in lost/stolen data, time off-line, reputation and the ransom itself has forced some companies to close. Ransomware attacks have become prevalent in the USA, with one happening every 14 seconds, according to research from Cybersecurity Ventures research firm.
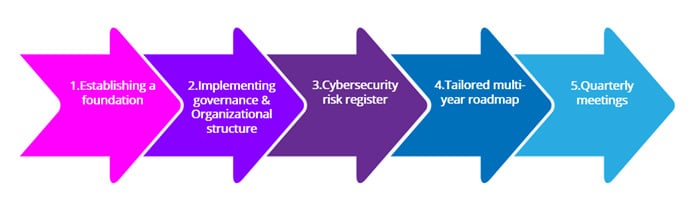
Multi-layered security measures should be established now, proactively, to bolster your cybersecurity strategy so that the company can either avoid being attacked or, in the event of an attack, the company should not suffer catastrophic loses. Continuous risk assessments and mitigation methods are crucial in identifying and dealing with potential ransomware threats proactively.
24/7 RansomAID Incident Response
While an attack is happening, you need to move quickly to minimize the damage, contain the threats and prevent further spreading of the malware. RansomAID’s incident response teams are immediately ready for any cyber incident. These nation-state grade security experts investigate ransomware incidents and reveal entry points, essential attack components and the evolution of each attack. This is crucial in the first few hours of an attack as it can completely change the outcome and prevent catastrophic loses.
RansomAID’s team typically provides focused recommendations on how to block the attackers and related route of access, how to improve security controls and countermeasures, and implementation plans of safeguards going forward.
Detailed threat map identifying company’s cyber-threat landscape – externally and internally.
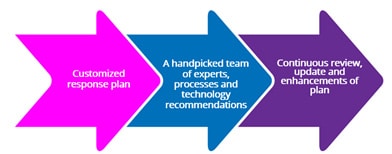
Customized response plan for incidents.
24/7 advanced detection technologies, preventative countermeasures, and deceptive techniques.
Handpicked team of experts is assembled to handle live incidents, and evolving threats are met 24/7.
Unique forensic analysis techniques to analyze all assets – disk, memory, and networks.
Infected network areas/endpoints/user IDs are isolated from the rest.
Remediation plans are actionable bullet points to ensure time to remediation is as quick as possible. We focus not only on the immediate threat but build a complete threat and ransomware strategy to help reduce the company’s attack surface for the future.
© 2025 Holistic Cyber (HolistiCyber). All Rights Reserved. Privacy Policy