Risk registers are a vital tool for cybersecurity planning that consolidate business risks into a single, manageable space. They provide streamlined reporting and information to align teams around the most important initiatives and will help save resources, time, and labor. By integrating compliance standards, defining the boundaries of needed coverage, and the likely effectiveness of various measures, a risk register becomes an indispensable asset, enabling security teams to fortify their cybersecurity defense.
What is a Risk Register?
A risk register is a comprehensive repository that gathers and systematically records information about risks over time. A good risk register continues compiling data over time, providing a historical record of the identified risks, their evolution, and any mitigation actions taken to address them.
What To Include in Your Risk Register:
- Risk Identification: Clearly articulate potential risks that could impact your cybersecurity, considering factors like data breaches, system vulnerabilities, or third-party dependencies.
- Risk Assessment: Evaluate the likelihood and potential impact of each identified risk. Use a standardized scale to quantify and prioritize risks based on severity.
- Mitigation Strategies: Outline specific actions or controls to address and reduce each risk. This section should detail preventive measures and incident response plans.
- Responsibility Assignments: Clearly define who is responsible for managing and mitigating each identified risk. This ensures accountability within the team.
- Monitoring and Reporting: Establish a system for continuous monitoring of identified risks and regular reporting to keep stakeholders informed.
What Not To Include in Your Risk Register:
- Excessive Detail: Avoid drowning the register in unnecessary minutiae. Focus on high-level risks and strategic mitigation rather than getting lost in overly detailed information.
- Generic Language: Steer clear of vague or generic statements about potential risks. Be specific about the nature of each risk and the corresponding mitigation strategies.
- Overemphasis on Unlikely Risks: While it’s crucial to identify potential threats, avoid overemphasizing improbable scenarios that may distract from more pressing concerns.
- Unclear Terminology: Use clear and concise language. Avoid jargon that may confuse stakeholders who are not cybersecurity experts.
- Outdated Information: A static risk register becomes outdated quickly. Regularly update and reassess the register to ensure its relevance.
Steps to Create a Risk Register
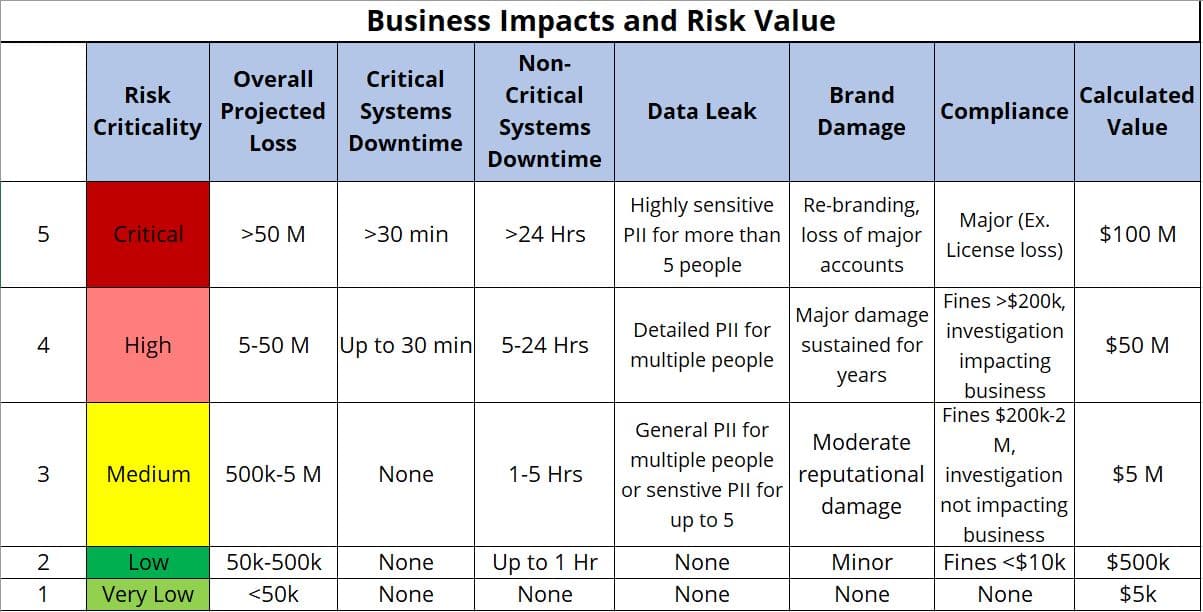
- Business Impact Analysis (BIA): Begin by conducting a thorough Business Impact Analysis (BIA), assessing the potential consequences of cybersecurity risks on critical business functions, operations, and overall organizational objectives. This foundational step provides a clear understanding of the potential impact each risk might have on the business.
A Business Impact Analysis shows the likely financial and business losses resulting from a cyber breach, sorted by criticality. - Identify Risks: Systematically identify potential risks by analyzing the organization’s entire digital ecosystem, considering factors such as data vulnerabilities, system weaknesses, and external threats.
- Assess Risks: Evaluate the likelihood and potential impact of each identified risk, utilizing a standardized scale or methodology. This step requires both a quantitative and qualitative analysis to prioritize risks based on severity. When assessing risk levels, it’s important to consider possible compliance issues. However, it’s also important to go beyond that and consider the motivations and standard methodologies of potential attackers. Understanding how attackers work and think will help your organization allocate resources more effectively to safeguard against the tactics they are most likely to employ. Assign each risk a criticality level, to help guide your allocation of resources and attention.
- Prioritize Risks: Prioritize each risk based on the criticality level, severity, likelihood, and potential consequences. This step ensures that attention and resources are directed toward mitigating the most critical and impactful cybersecurity risks first.
- Define Mitigation Strategies: Develop specific and targeted mitigation strategies for each identified risk, outlining detailed actions to address vulnerabilities and reduce the likelihood or potential impact of an incident.
- Assign Responsibilities: Clearly assign responsibilities to individuals or teams for the management and mitigation of each identified risk. Clearly outline who would be responsible for taking what actions and when. This step creates accountability and a well-defined action plan, facilitating effective and timely responses to potential cybersecurity threats.
- Monitor and Review: Establish a continuous monitoring process to regularly review the risk register, updating it to reflect changes in the cybersecurity landscape. This ongoing assessment ensures that the organization remains agile in addressing emerging threats and evolving risks.
- Communicate with Stakeholders: As with all cybersecurity planning, it’s important to maintain transparent communication with relevant stakeholders, providing regular updates on identified risks, ongoing mitigation efforts, and any changes to the risk register. This step fosters a collaborative and informed approach to cybersecurity, aligning all parties with the organization’s risk management strategy.
Enhancing Your Risk Registry with SAGE
The best way to elevate your risk registry is by using a cyber defense planning and optimization platform. Used properly, a CDPO platform like SAGE can play a pivotal role in deciphering and prioritizing cyber defense tasks based on risk reduction.
SAGE goes beyond conventional risk registers by using the information to perform comprehensive risk calculations and evaluating the potential impact of each identified risk. This calculation becomes the cornerstone for building a cyber defense plan. By understanding the potential impact and likelihood of each identified risk, SAGE empowers CISOs to prioritize tasks effectively.
Prioritizing Tasks for Optimal Cyber Defense
While there are various methods to prioritize tasks, SAGE simplifies the process by considering how much it reduces the risk. If two possible options have similar costs, SAGE will guide the CISO to focus on the one that offers greater risk reduction. This approach ensures that resources are strategically allocated to address the most critical cybersecurity concerns.
For many of the current SAGE users, the platform serves as their primary risk register. This of the risk register into the Cyber Defense Planning and Organization platform allows for a unified approach, streamlining risk management and defense planning and eliminating the need for an additional tool.
For those who already have a separate risk register, SAGE enhances its value through integration. It reads data from an existing register, leveraging the information to perform precise risk calculations.
Additional Best Practices For Creating and Managing a Risk Register
Leverage Threat Intelligence Integration: If possible, integrate threat intelligence sources into your risk register to harness real-time data on emerging threats. This not only enhances the accuracy of risk assessments but also keeps your organization alert to new potential threats.
Use A Red Team to find new vulnerabilities: Employ a red team to simulate potential attackers attempting to breach your systems. This will help identify vulnerabilities that may be overlooked in traditional risk assessments. This practice will provide a new perspective on the assets you are trying to protect, and possibly uncover hidden risks and help strengthen your organization’s overall cybersecurity posture.
Consult with cybersecurity experts : Navigating the complex terrain of cybersecurity risk management can be a daunting task. If you’re looking to elevate your risk register and fortify your defenses, consider seeking expert assistance.
To learn more about how SAGE can enhance or replace your existing risk registry, or to see a demo of the platform, contact us today.